Hello aspiring bug bounty hunters! I’m Jivan, and I’m back with another security vulnerability that I discovered in an Android app. In this write-up, I will explain one of my findings related to GCP (Google Cloud Platform) — specifically, hardcoded Google Cloud service account credentials found in the app binary, which allowed me to gain control over the associated Google Cloud project.
Now let’s start with how I found and gained access to GCP in [Redacted Android App]. Due to security reasons, I can’t disclose the application name or company details. Instead, I will refer to the target app as [Redacted Android App] throughout this write-up.
After that, I downloaded the [Redacted Android App] from the Play Store to my emulator, then pulled the APK file to my host machine for static analysis.
After this, I used Apktool to decompile the APK in order to access the app’s binary and source code. I then started exploring the source code of [Redacted Android App]. The decompiled structure included several folders such as smali files, the AndroidManifest.xml file, assets, resources, and other related files.
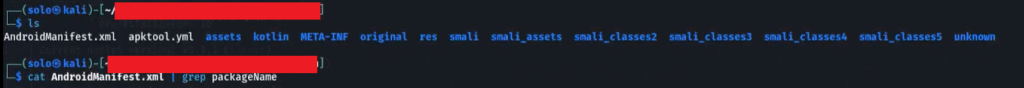
After that, I began my analysis by looking into the most common files, such as AndroidManifest.xml and strings.xml, but I didn’t find any interesting details there. I then checked other files like smali and unknown, but they also didn’t contain any useful information. Interestingly, when I opened the assets folder, I noticed that it contained a few files in different formats. What caught my attention were the files with the .json extension they looked interesting, so I decided to investigate them further.

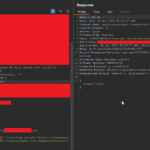
After noticing the JSON files, I ran the cat command to display their contents. Upon reviewing the output, I confirmed that these JSON files contained Google Service Account credentials — including fields like project_id, private_key_id, private_key, client_id, client_email, and other details essential for a developer to connect to Google Cloud.

After seeing this information, I immediately copied the .json file to another location because configuring the key with the Google Cloud command-line tool (gcloud) requires it.
After that, I ran the following command to activate the service account for the leaked key: gcloud auth activate-service-account --key-file=data_tracking_qa_app_distribution.json This command configures gcloud to use the specified service account key.
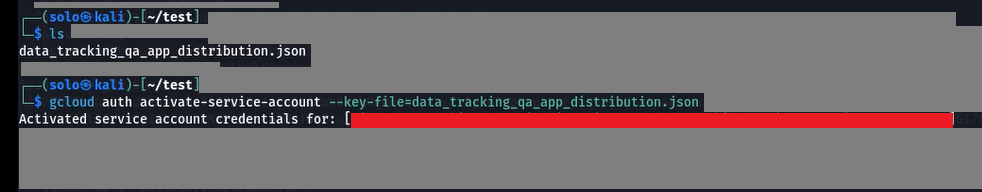
As you can see in the screenshot above, the gcloud tool is configured with the supplied credentials.
Sorry, I also grayed out the other parts of the screenshot because there was sensitive information in the background. That’s why the rest of the area is grayed out.
After that, I ran the gcloud auth print-access-token command. This command prints the access token of the configured account.

The above access token already proves that the leaked key is active and vulnerable. However, to demonstrate the full impact, I proceeded with further investigation.
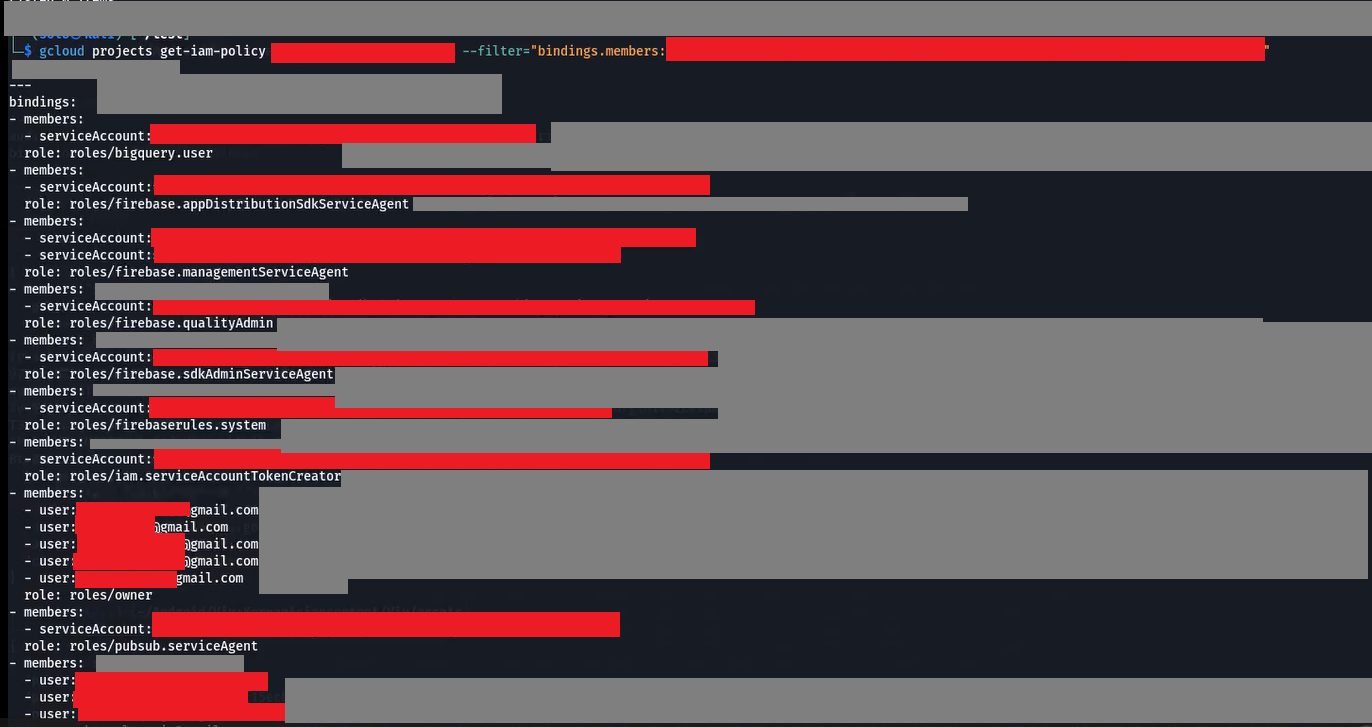
After that, I ran another command to list the service account roles and other permissions: gcloud projects get-iam-policy --filter="bindings.members:SERVICE_ACCOUNT_EMAIL" I executed this command by providing the correct project ID and service account email to retrieve the list of all permissions and roles associated with the IAM policy.
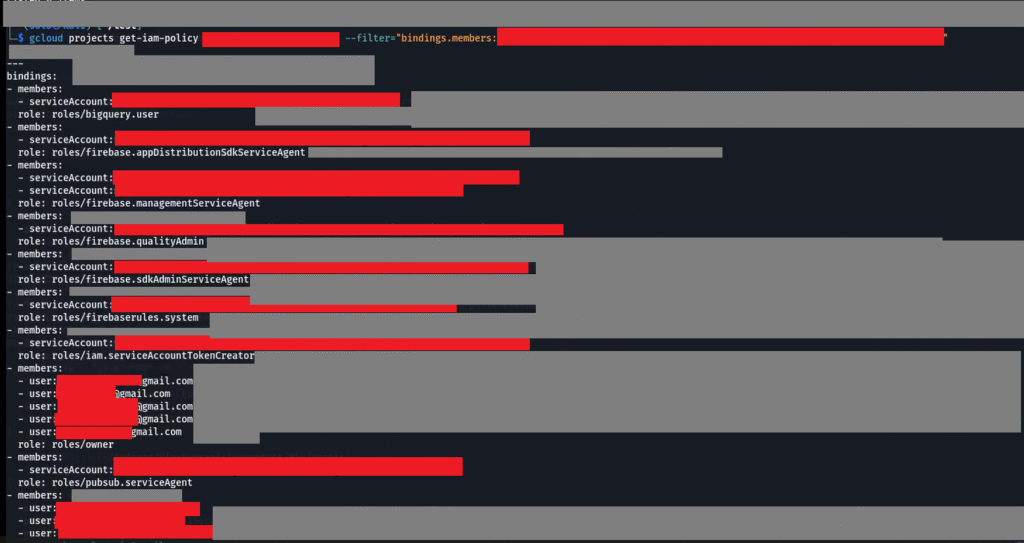
After running the above get-iam-policy command, I was able to confirm full access to the leaked Google service account. This command returns the roles assigned to a specific user. I have grayed out parts of the output due to security reasons.
If you look closely, you’ll see that I was also able to access the email ID of the user working with this service account, which makes this a solid finding.
After that, I ran another command to find the exact roles assigned to the leaked Google service account credentials: gcloud projects get-iam-policy --flatten="bindings[].members" --format='table(bindings.role)' --filter="bindings.members:SERVICE_ACCOUNT_EMAIL" This command lists the specific roles associated with the service account.
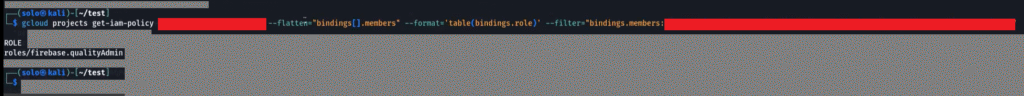
So, the leaked credentials JSON file or more specifically, this service account has the Firebase QualityAdmin role.
After gathering all the findings and proof of concept, I submitted a comprehensive security report to the company. I also mentioned that the rest of the JSON files contained leaked credentials as well. However, to maintain trust between the company and me, I only tested one key. The company fixed the others accordingly.
Later, the triager reviewed my report, classified it as Critical severity vulnerability, and rewarded me with a bounty of $700 USD.
🎯 Run Your Bug Bounty Program with Cyberbay — Use My Referral Code
If you’re part of a company or security team planning to launch a bug bounty program, Cyberbay is a fantastic platform to consider. I’ve had a great experience working with them as a researcher, and I highly recommend their platform for managing security reports and collaborating with ethical hackers.
As a valued member of the Cyberbay community, I’m excited to share an exclusive referral code for companies:
👉 Use referral code JIVAN2025 during registration to receive 15% off your company’s first purchase on Cyberbay.
🔐 Ready to get started? Register your organization here: https://community.cyberbay.tech/signup/corporate
Whether you’re a startup or a large enterprise, launching a bug bounty program is a smart step toward strengthening your security. Don’t miss this opportunity to launch your program with a discount and the support of a growing security community!
Have questions about the process? Feel free to reach out — I’m happy to help you get started.
🚀🙏 Thank You for Reading!
I hope you found this write-up on the exposed Google Cloud service account credentials insightful and informative. My goal is to share real-world bug bounty experiences to help others in the security community learn and stay sharp.
If this report gave you a new perspective or taught you something useful, stick around — I’ll be sharing more deep-dive write-ups on Web, Android, and iOS security vulnerabilities soon!
Got questions, suggestions, or feedback? Feel free to drop them in the comments.
Until next time — keep hacking, stay curious, and always respect the scope! 🎯🔐