Hello friends, I’m Jivan, and I’m back with another write-up about a Google Cloud Storage Bucket Misconfiguration vulnerability. In this case, I was able to spider the bucket and access user-uploaded photos.
In this write-up, I will explain how I discovered this vulnerability and how I was able to access user media files.
Now, let’s get started. This is an adult messaging website where I discovered the vulnerability.
Due to security reasons, I cannot disclose the company name or target details, so I will refer to it as [Redacted Dot Com], where this vulnerability was identified.
Now, after this, I visited [Redacted Dot Com] and started testing the web application. I created an account and tested various endpoints like login, attempted to bypass authentication, and also tested for CSRF vulnerabilities. I then checked for Broken Access Control (BAC) and other common issues, but found no vulnerabilities.
After that, I examined the source code of the web application and searched for keywords like “token”, “key”, “admin”, and “internal”, but found no relevant details confirming that there were no obvious issues on the site.
I then tested for IDOR (Insecure Direct Object Reference) vulnerabilities again on [Redacted Dot Com], but this also failed. I even searched for any sensitive information in public forums and tried using Google Dorks, but had no luck which confirmed that [Redacted Dot Com] appeared to be very secure.
However, after some more testing, I revisited the source code, and interestingly, I found something like a Google Cloud Storage Bucket related to [Redacted Dot Com]. This vulnerability has since been fixed, and unfortunately, I didn’t take a screenshot to show exactly where the bucket name was located in the source code.
So, I will now refer to my further testing images to demonstrate how I found and accessed the user’s photos.
So, the actual hardcoded bucket Name was found by its name, which was present in the source code like this:{"Google_Storage_Bucket":"media.redacted.com"} (Note: I have altered the bucket name for security reasons.) The naming convention clearly indicates that this is a Google Cloud Storage Bucket.
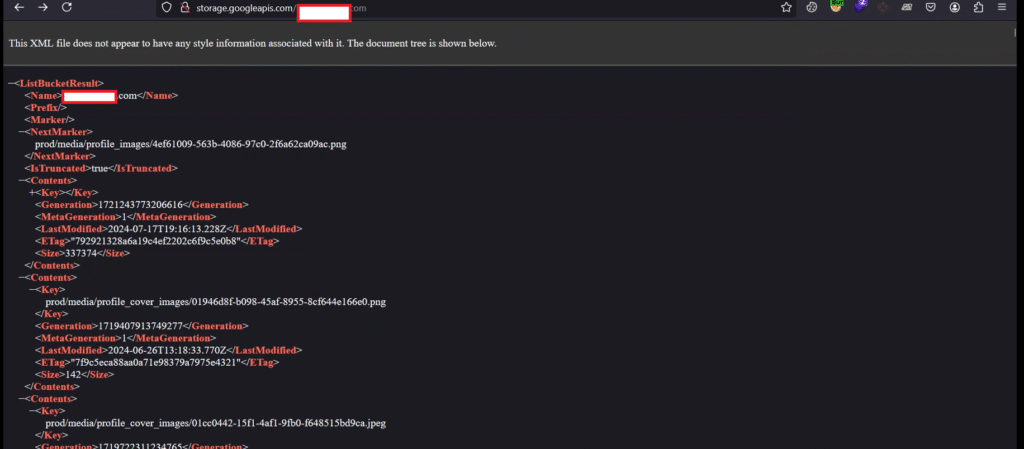
After that, I created a URL to view the objects present in the media.redacted.com bucket like this:https://storage.googleapis.com/media.redacted.com
I opened this URL in a web browser and found that it was leaking objects, which confirms that the bucket was publicly accessible and vulnerable.
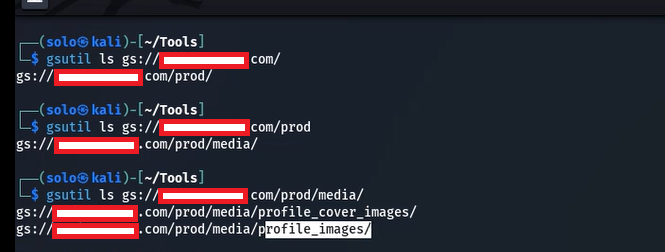
After finding this, I tested the bucket further using the gsutil tool. I ran the following command to list the top-level objects in the bucket: gsutil ls gs://media.redacted.com/
After running this, I saw a /prod endpoint, which is also visible in the screenshot above
After this, I ran another command to find the object list for the /prod endpoint using: gsutil ls gs://media.redacted.com/prod this returned /media as the next endpoint path.
Now, I ran the command: gsutil ls gs://media.redacted.com/prod/media/ and it returned two different directories: /profile_images and /profile_cover_images
Now, I ran the following command: gsutil ls gs://media.redacted.com/prod/media/profile_images and it returned a large number of user profile photos and other images.
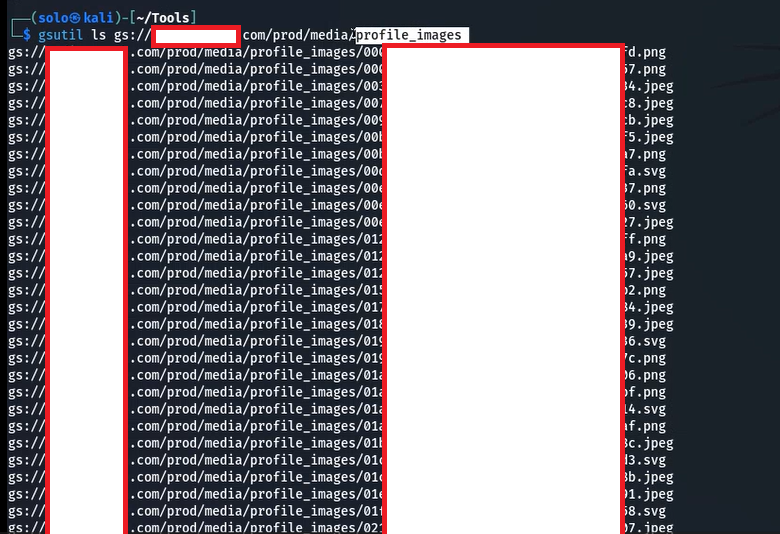
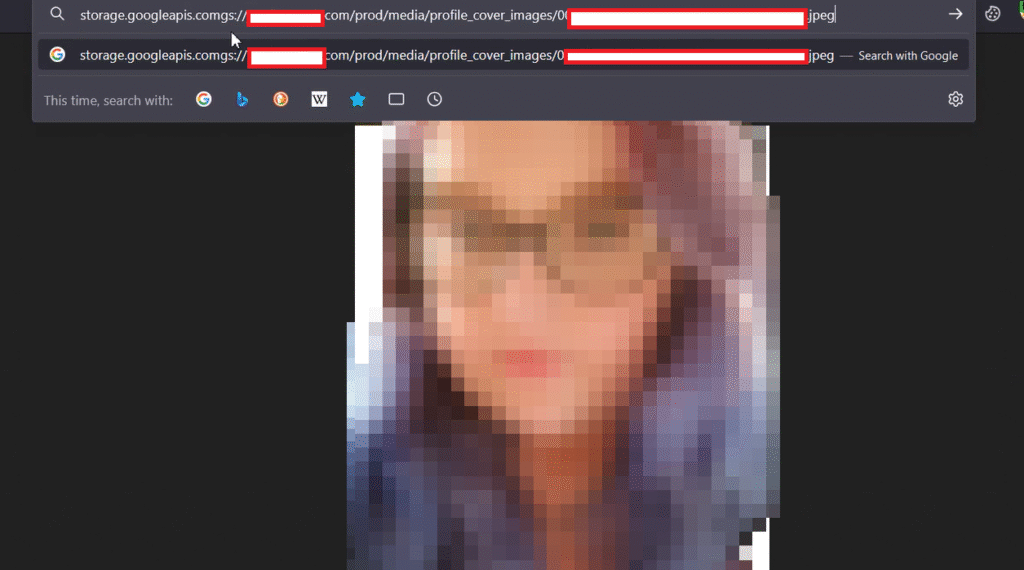
After this, I opened a few images, which revealed user profile pictures and private photos.
After completing all the testing and confirming that the vulnerability existed which allowed me to view and spider the entire Google Cloud Storage Bucket I prepared a detailed report and submitted it to the triage team. Within a few hours of submission, I received a reply from the team confirming that the vulnerability had been fixed. They classified it as a Low severity issue and rewarded me with a bounty of $250 USD for this finding.
🙏 Thank You for Reading!
I hope this write-up about the Google Cloud Storage Bucket misconfiguration helped you understand how even small mistakes in cloud settings can lead to serious data leaks.
I’m sharing real-life security findings so others can learn from them in a clear and simple way — with a focus on practical examples that matter.
If this report helped you learn something new or made things clearer, stay tuned! I’ll be posting more detailed write-ups on website and Android soon.
Feel free to share your thoughts, feedback, or questions — I’m always happy to hear from you.
Until next time, stay curious, keep learning, and always be responsible online. 🔒🌐