Welcome to my very first bug bounty write-up!
Hi, I’m Jivan — a passionate self-taught security researcher from India, and this is my very first public bug bounty write-up.
After spending months exploring mobile security and diving deep into Android applications, I finally decided to share my journey with the community. This write-up is not just about the vulnerability I discovered, but also about how I think, test, and approach mobile app security — especially from the perspective of someone still learning and growing in the field.
In this case, I found an OTP bypass vulnerability in an Android app that earned me a €150 bounty, and more importantly, boosted my confidence to share what I know. I hope this helps others who are just starting out in Android pentesting or looking to find real-world bugs.
Now let’s get started. This is one of my older findings where I discovered an OTP bypass vulnerability in the account registration process. Let me explain it in detail for you.
First, I downloaded the target Android app from the Play Store onto my emulator. Due to security reasons, I can’t disclose the application’s or company’s name, so I’ll refer to it as [Redacted App] throughout this write-up.
After installing the [Redacted App], I configured the Burp Suite proxy and began dynamic analysis. Initially, I tried opening the app without bypassing SSL certificate validation to check whether it was using SSL pinning. I confirmed that SSL pinning was in place.
To bypass this, I used Frida along with a Frida JS script. After successfully bypassing SSL pinning, the app launched on the emulator. However, I noticed that Burp Suite was still not capturing any traffic from the app.
Suspecting root detection, I tested further and confirmed that the app also had root detection mechanisms enabled. Because of this, I stopped using the Frida script and switched to the Objection tool, which can bypass both SSL pinning and root detection.
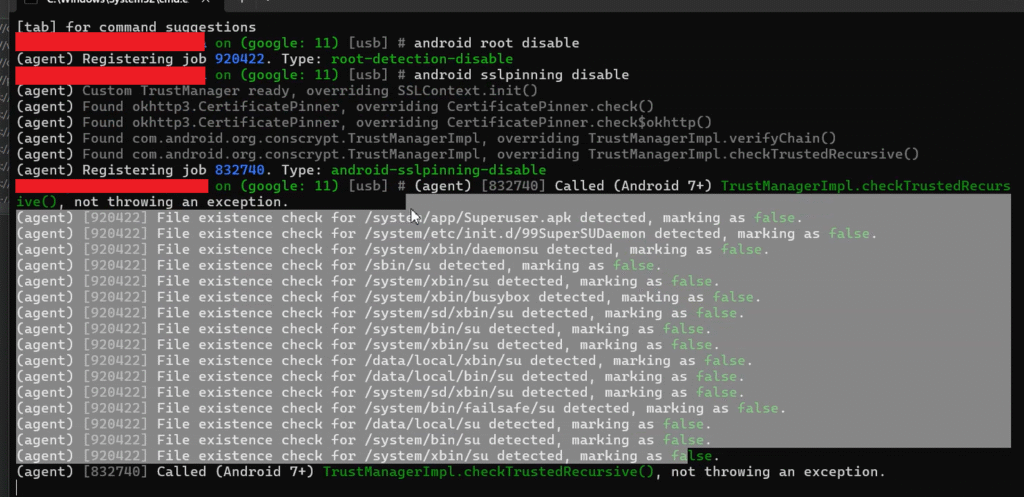
After using Objection, I successfully bypassed both protections and was finally able to intercept the app’s traffic in Burp Suite.
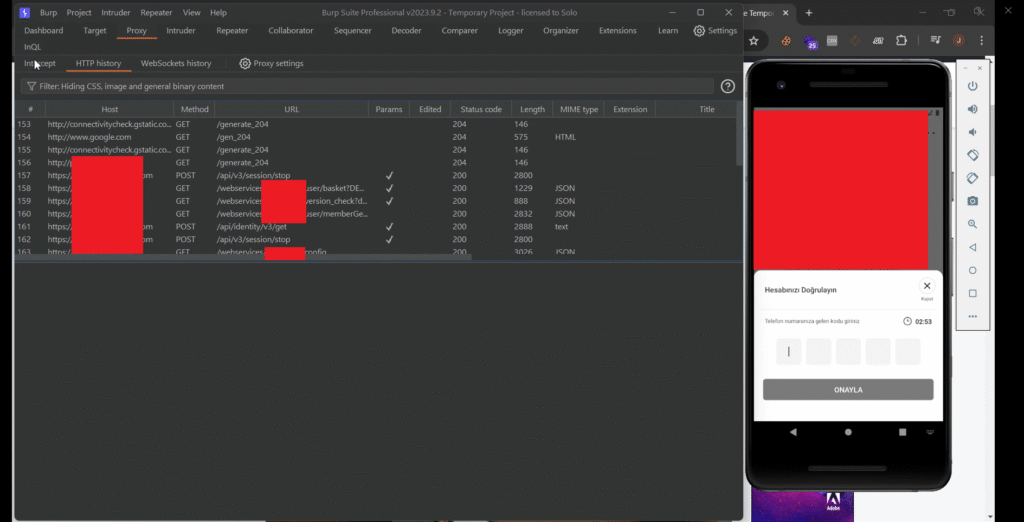
After bypassing root detection and SSL pinning, I was able to access the registration activity — and this part turned out to be quite interesting.
The app is not intended for users in my region and only allows phone numbers from a specific country to register. First, I attempted to register using a disposable phone number, but had no luck — I couldn’t find a disposable number for the target country.
I proceeded to fill in the required registration details such as email, first name, last name, and a phone number. Since I couldn’t find a valid disposable number, I searched online for the [Redacted App]’s country code and used a random phone number with the correct format.
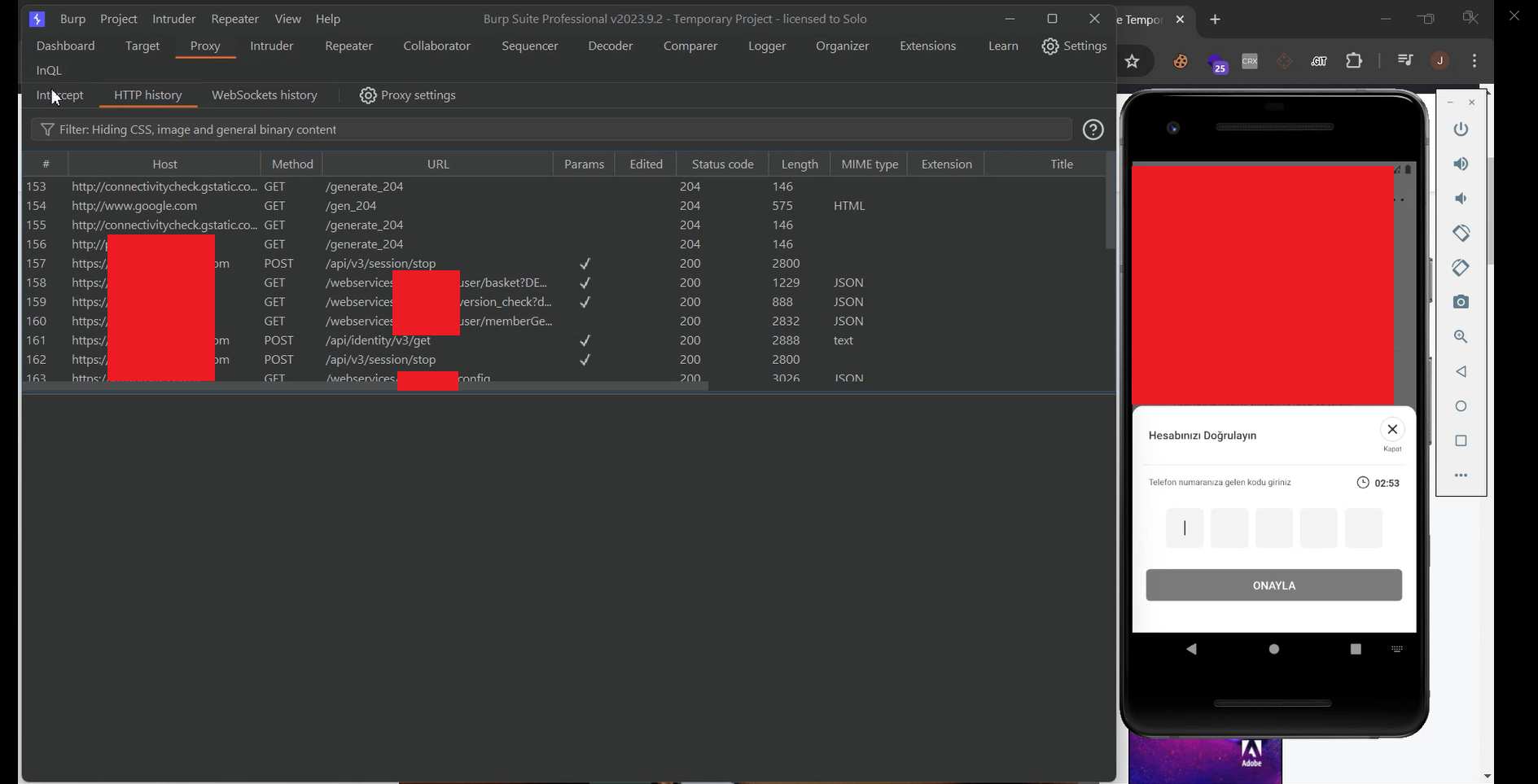
I confirmed that an OTP (One-Time Password) was sent to the supplied number — it was a 5-digit code. I then checked the HTTP history tab in Burp Suite to see if the OTP was being leaked on the client side (as is sometimes the case), but it wasn’t — which meant a valid OTP was required for account registration, and I had no control over the actual phone number.
As a next step, I entered a random 5-digit OTP and captured the corresponding POST request in Burp Suite to observe the response. The server returned a 422 Unprocessable Entity status code along with a JSON response.
{"error":true,"errorCode":"InvalidVerificationCode","message":"Do\u011frulama kodu ge\u00e7ersiz.","statusCode":422,"data":[]}
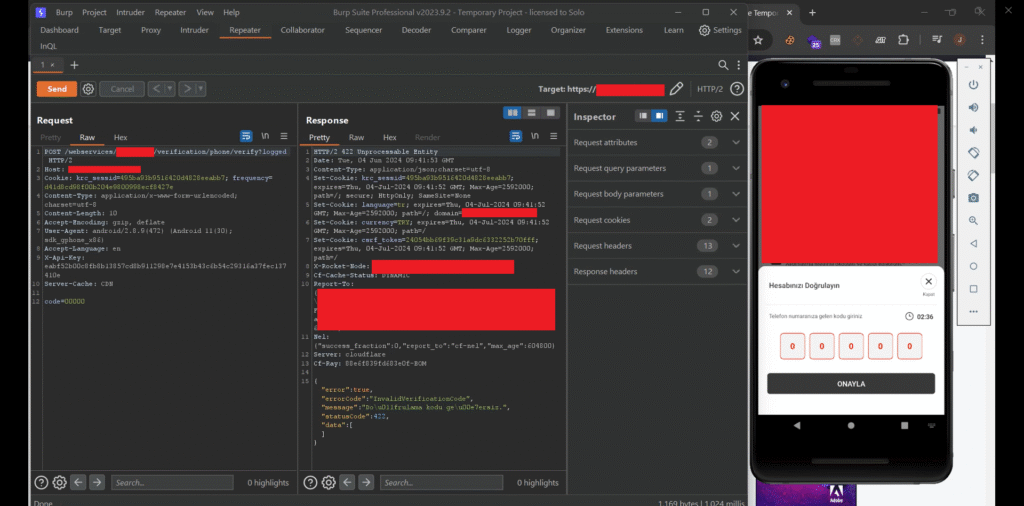
After seeing the server’s JSON response with an error and a statusCode, I suspected there might be a potential response manipulation vulnerability, although I wasn’t sure yet.
To investigate further, I re-entered an incorrect OTP and captured the OTP verification request in Burp Suite. I used the “Do Intercept” option to modify the response before it reached the app.
The original server response returned a 422 Unprocessable Entity status with an error message.
I modified the intercepted response as follows:
Changed HTTP/2 422 Unprocessable Entity to HTTP/2 200 OK
Changed "error": true to "error": false
Changed "errorCode": "InvalidVerificationCode" to "errorCode": ""
Changed statusCode: 422 to statusCode: 200
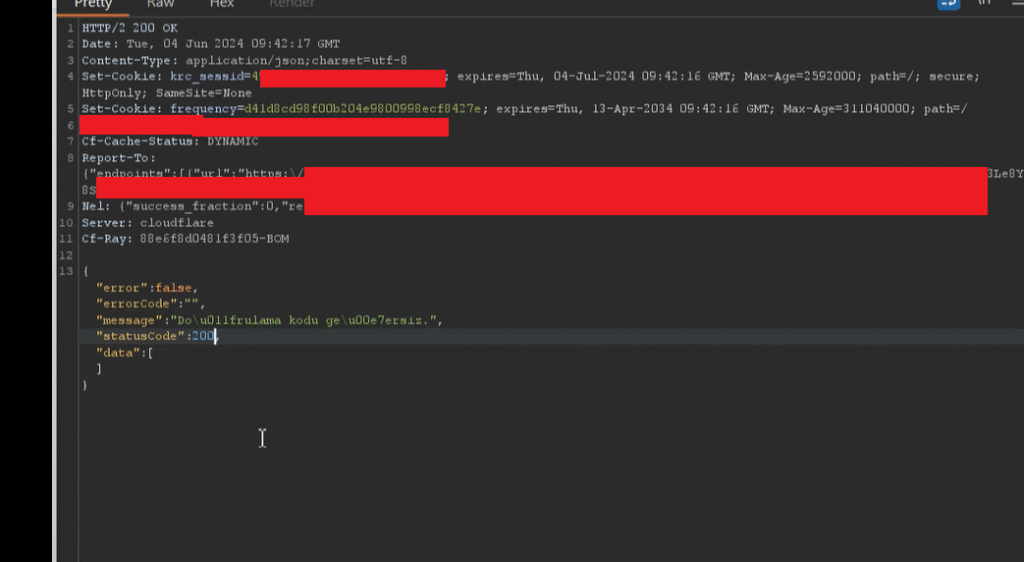
My goal was to see whether the app would treat this manipulated response as valid and allow the registration process to proceed.
After modifying the response, I forwarded the request and observed that the app processed it successfully — allowing me to bypass the OTP verification.
I then submitted a detailed report to the company, and it was accepted as a valid vulnerability with a medium severity rating. As a result, I was rewarded a bounty of €150.
🙏 Thank You for Reading!
I hope you enjoyed this write-up on the Android OTP bypass vulnerability. My goal is to share real-world findings in a simple and practical way that can help others in the security community learn and grow.
If you found this helpful or interesting, stay connected — more Android, iOS, and web exploitation write-ups are coming soon!
Feel free to share your thoughts or reach out if you have any questions. Until next time, happy hacking! 🔍💻
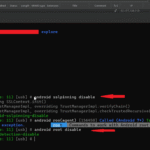
How to use objection tool to bypass both root detection and SSL pinning?
💡Hi! Thanks for reading the write-up and asking a great question.
To bypass both SSL pinning and root detection using Objection, start by installing it with
pip install objection. Once it’s set up, run the target app on a rooted emulator or device, and make sure Burp Suite is properly configured. Then, use the commandobjection -g explore to attach to the running app. Inside the Objection shell, runandroid sslpinning disableto bypass SSL pinning andandroid root disableto bypass root detection. This setup should let you intercept the app’s traffic in Burp Suite. Keep in mind that if the app uses advanced or custom security methods, Objection might not be enough — in those cases, using Frida with a custom script could be needed.Also, I’m planning to release a dedicated write-up soon that covers a complete Android lab setup for testing, so stay tuned for that