Posted inDesktop
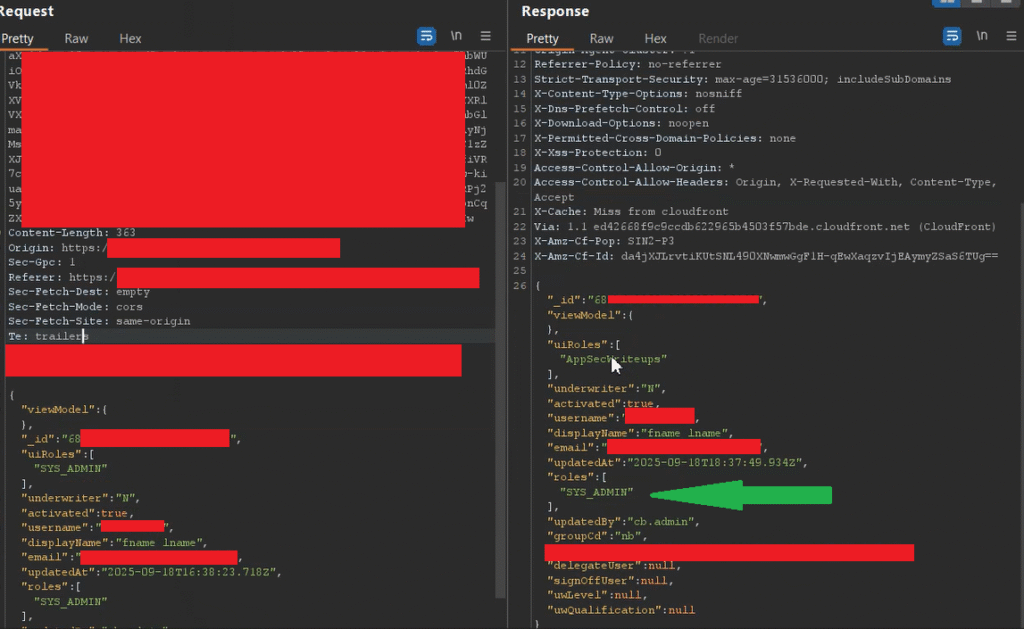
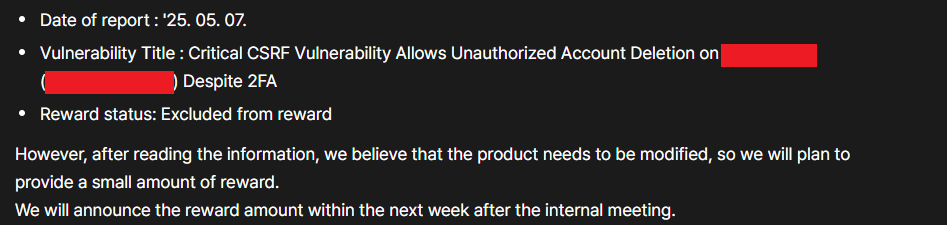
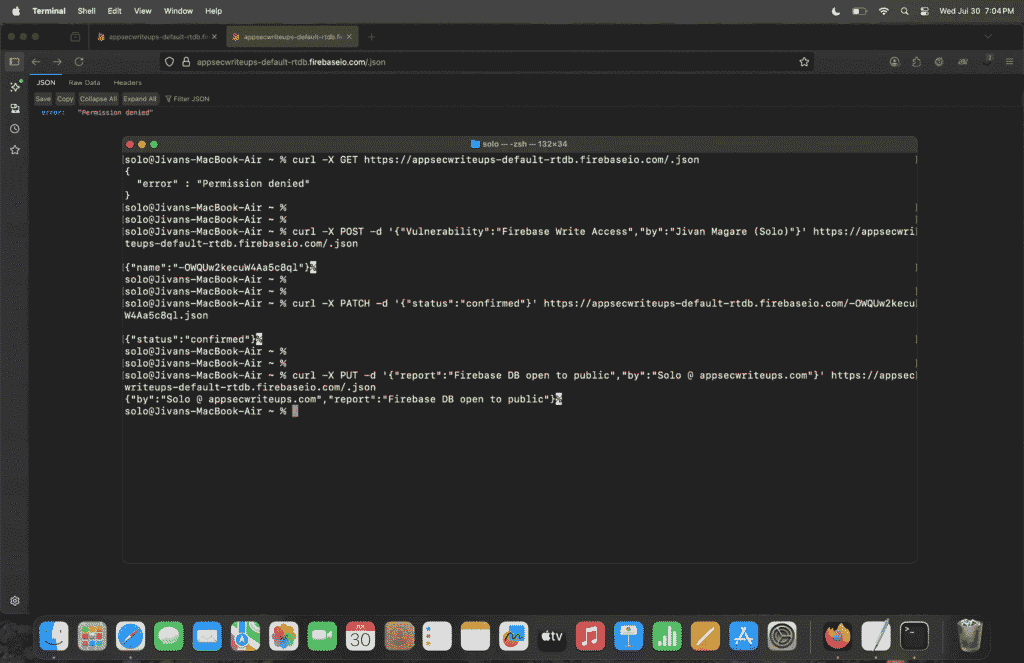
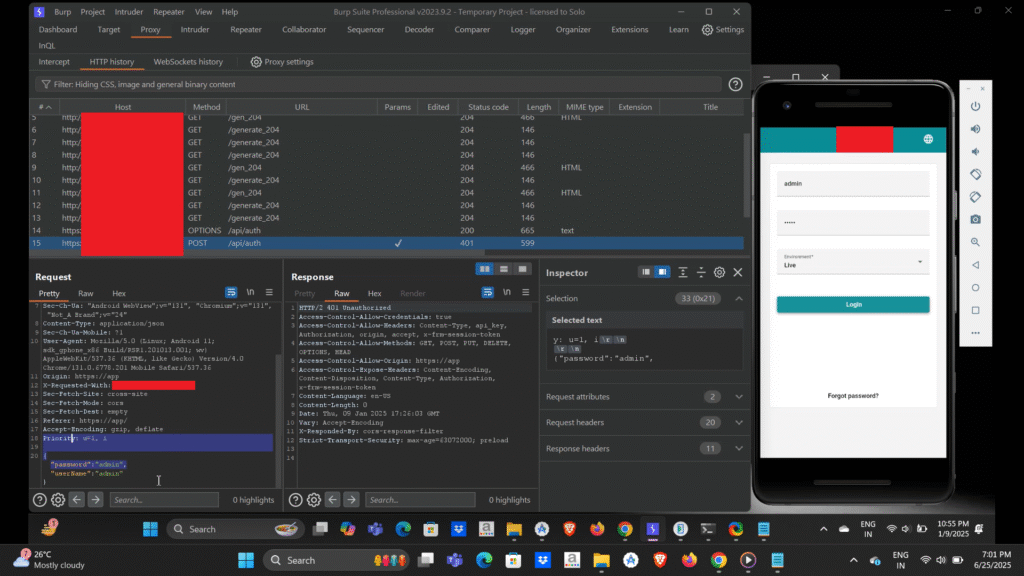
Protected: My First Day Pentesting Thick‑Client Apps — Discovered a Critical IDOR in a Desktop Client with a Full Black‑Box Approach
This content is password protected. To view it please go to the post page and enter the password.